This document will guide you through process of configuring Sinch as a telephony provider for your Okta organization.
- Okta Developer Edition organization
- Sinch account with enough credits
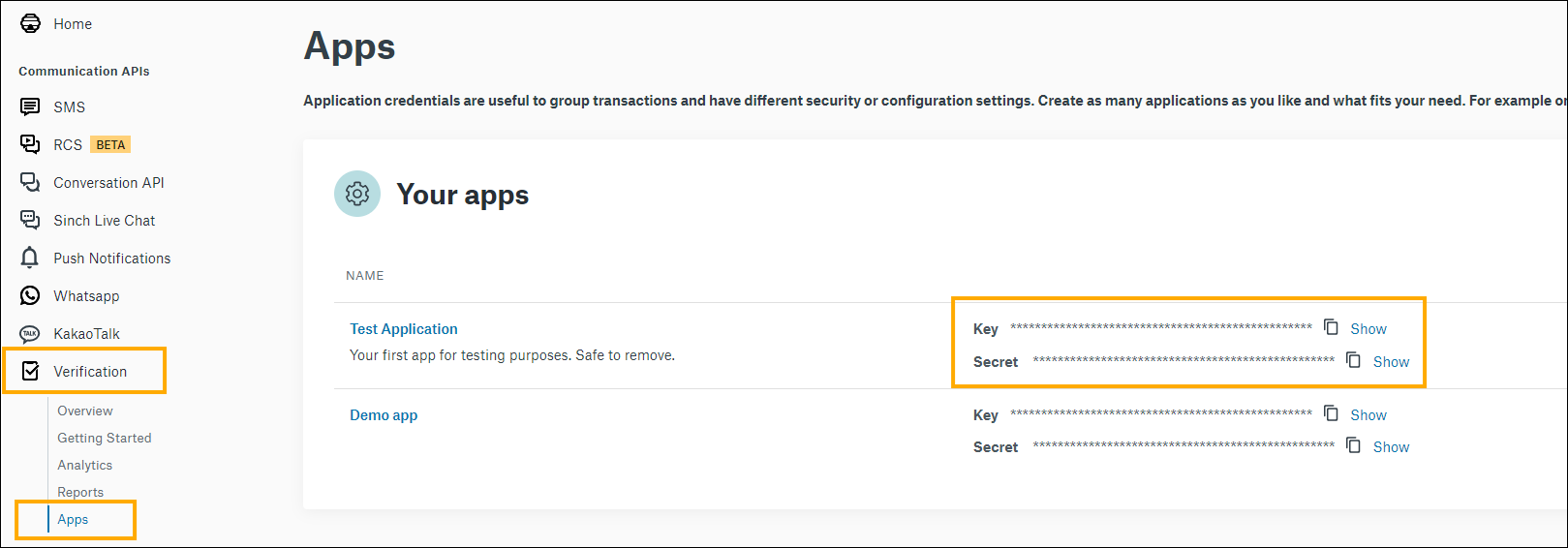
Go to Apps in the Verification section in Sinch dashboard. Grab the Key and Secret of the application you intend to use with Okta. You will need them in the next steps.
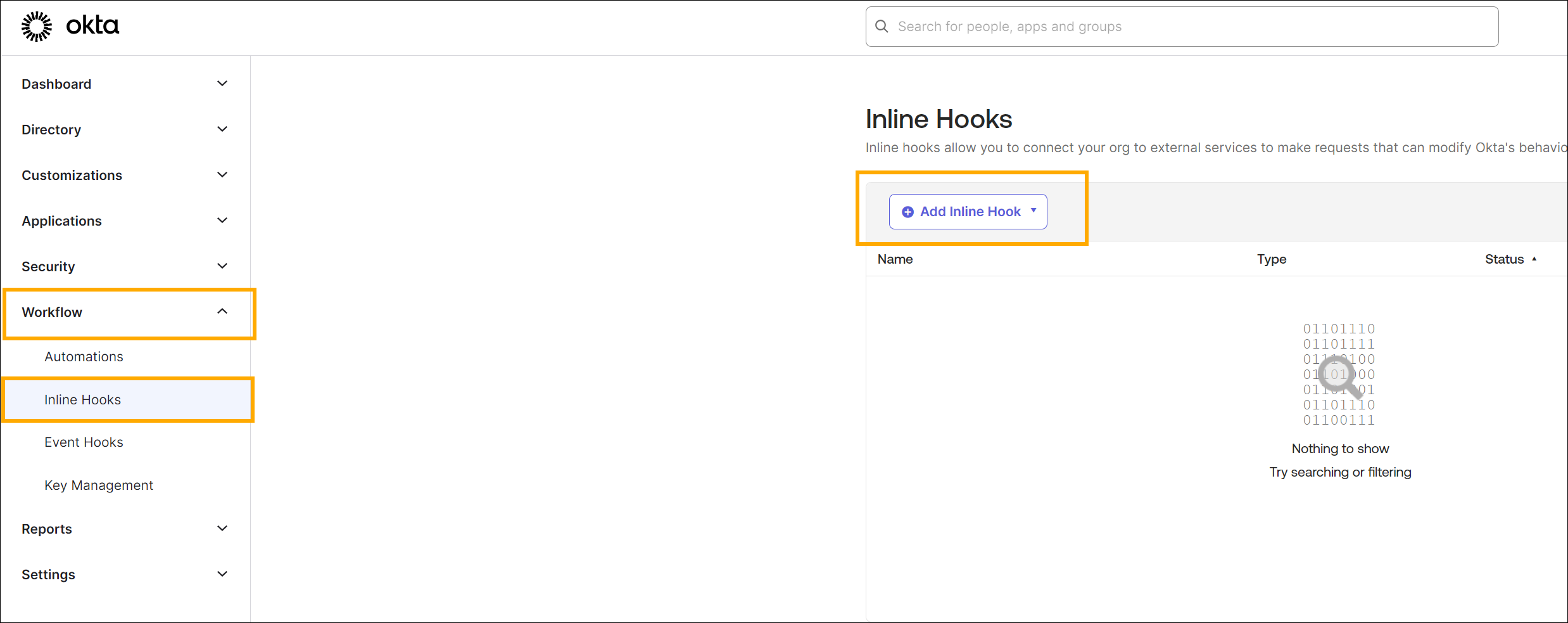
In the Okta Admin Console, navigate to Inline Hooks in the Workflow section. Click Add Inline Hook and select Telephony in the dropdown that appears.
In the Create Inline Hook form that appears next:
| Field | Description |
|---|---|
Name | Can be any value, but we suggest something that makes sense to you. |
URL | Must have the value of https://okta.verification.api.sinch.com/hook. |
Authentication field | Must have the value of Authorization. |
Authentication secret | Must adhere to the Basic authentication standard using the Sinch application key and secret. |
The rest of this guide assumes Sinch was used for Name.
The Basic authentication standard dictates that key and secret must be encoded as Basic base64(key:secret), where Basic is a literal, key and secret are Sinch credentials collected earlier, and base64 is an encoding function.
Avoid using base64 encoding tools available online as they might leak your secrets. As a safe alternative, operating system, native tools can be used. For instance on Windows using Powershell:
$ApplicationKey="key from Sinch dashboard"
$ApplicationSecret="secret form Sinch dashboard"
$Token=$("${ApplicationKey}:${ApplicationSecret}" | % { [Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($_)) })
Write-Host "Basic ${Token}"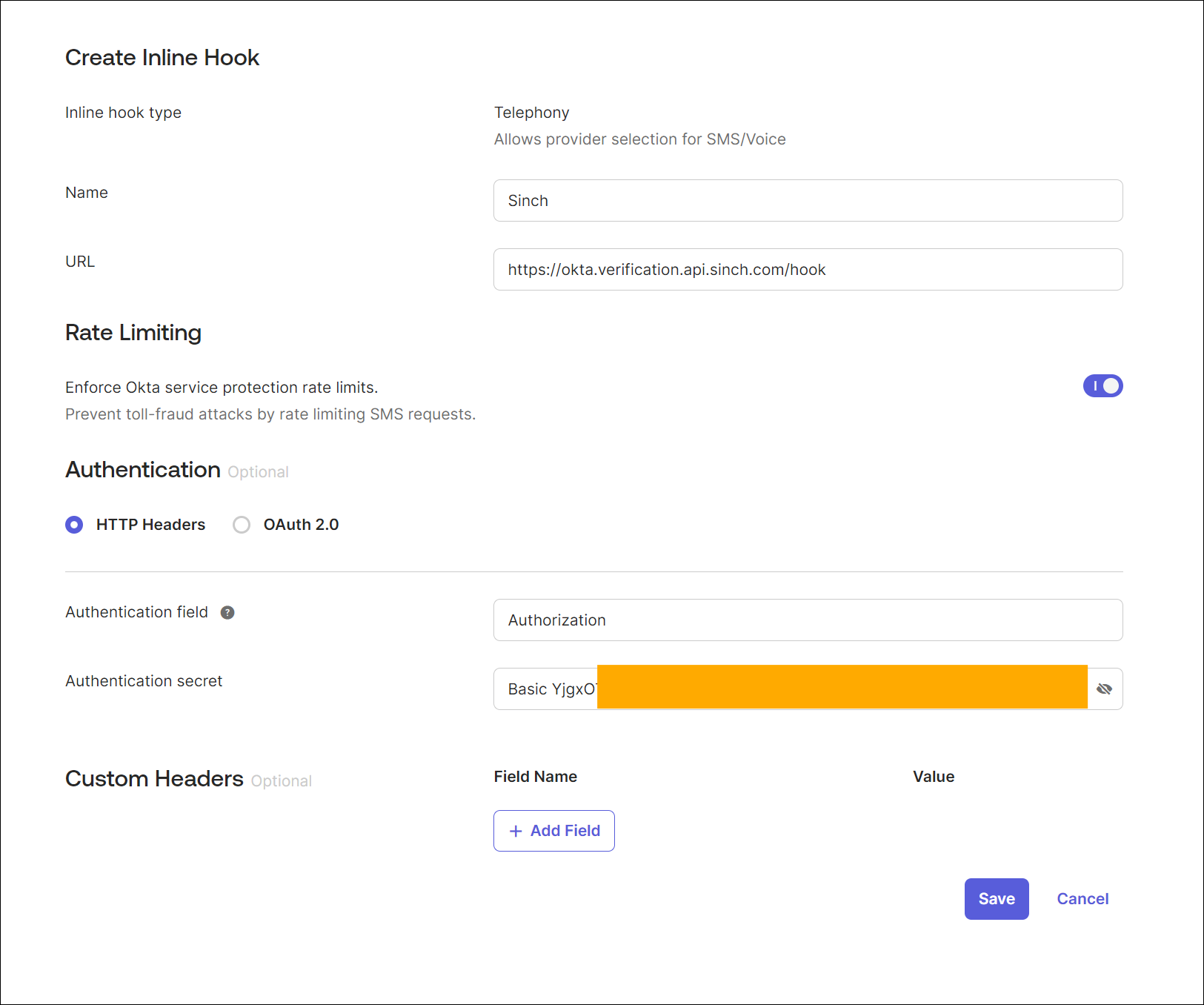
Pay special attention to leading and trailing whitespace (space, tab, line break) characters when filling in the form!
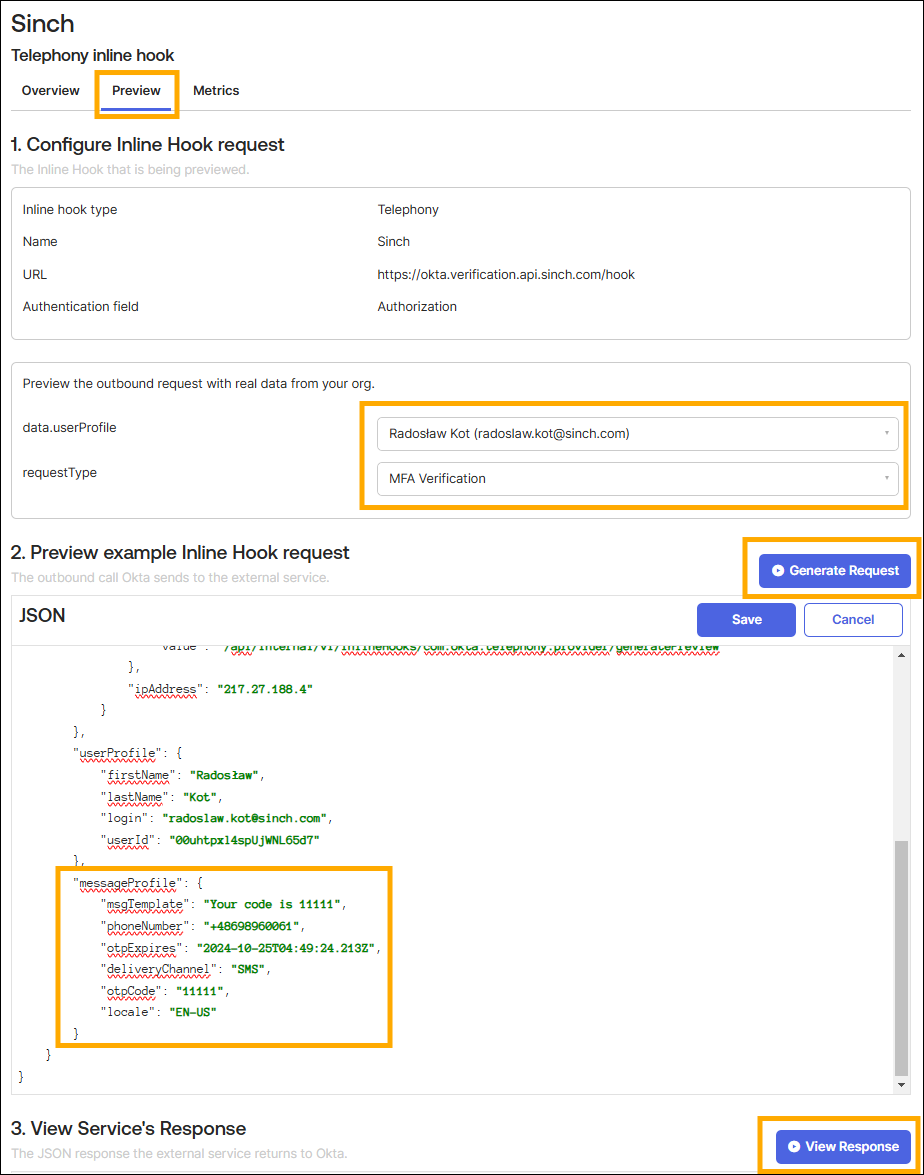
In the Preview tab:
- Select a user to test the hook with.
- Select
MFA Verification. - Click
Generate request. - Review data in generated JSON:
phoneNumbermust include country calling code,- code in the
msgTemplatemust matchotpCode, deliveryChannelmust beSMS.
- Click
View response.
In the Preview tab:
- Select a user to test the hook with.
- Select
MFA Verification. - Click
Generate request. - Review data in generated JSON:
phoneNumbermust include country calling code,deliveryChannelmust beVoice,localeshould specify desired language.
- Click
View response.
The Customization section at the end of this document provides more information about configuring both delivery methods.
To use the created hook in the authentication pipeline, navigate to Authenticators and click Add authenticator.

Select Phone and review the options in the Add Phone dialog.
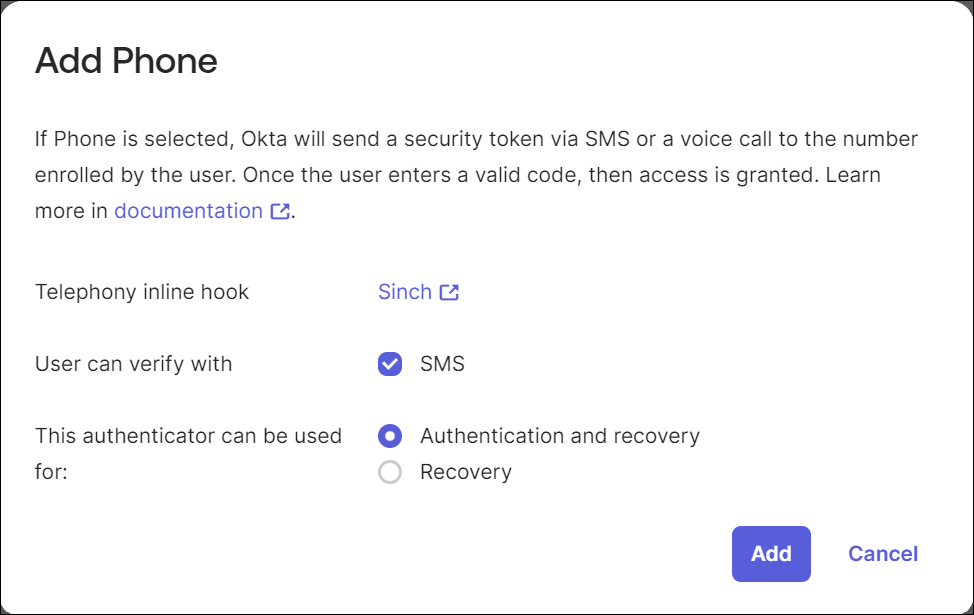
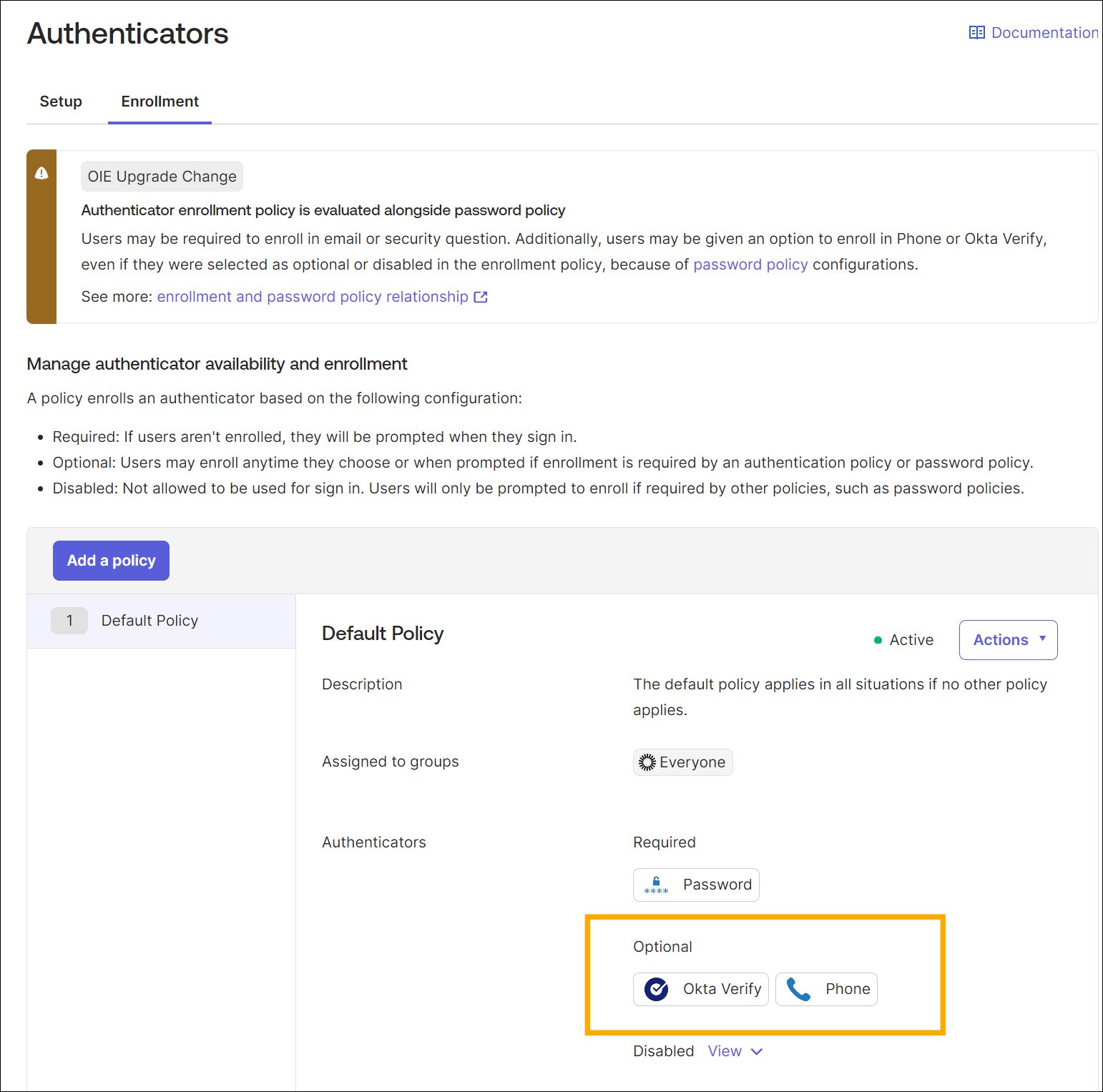
Configure the newly added Authenticator in the Enrollment tab according to your needs.
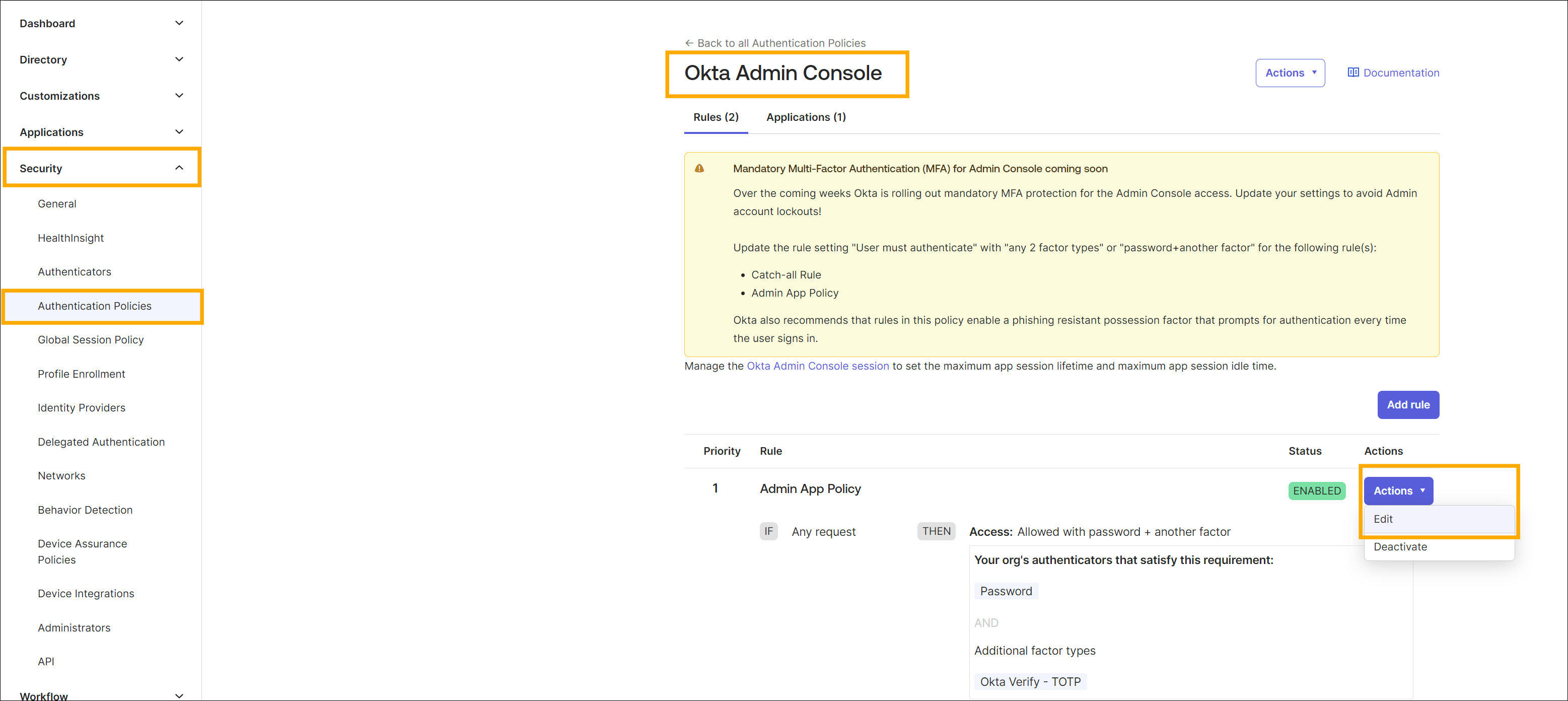
In the Authentication Policies configure selected policies to use Phone Authenticator by clicking Edit as shown in the screenshot below.
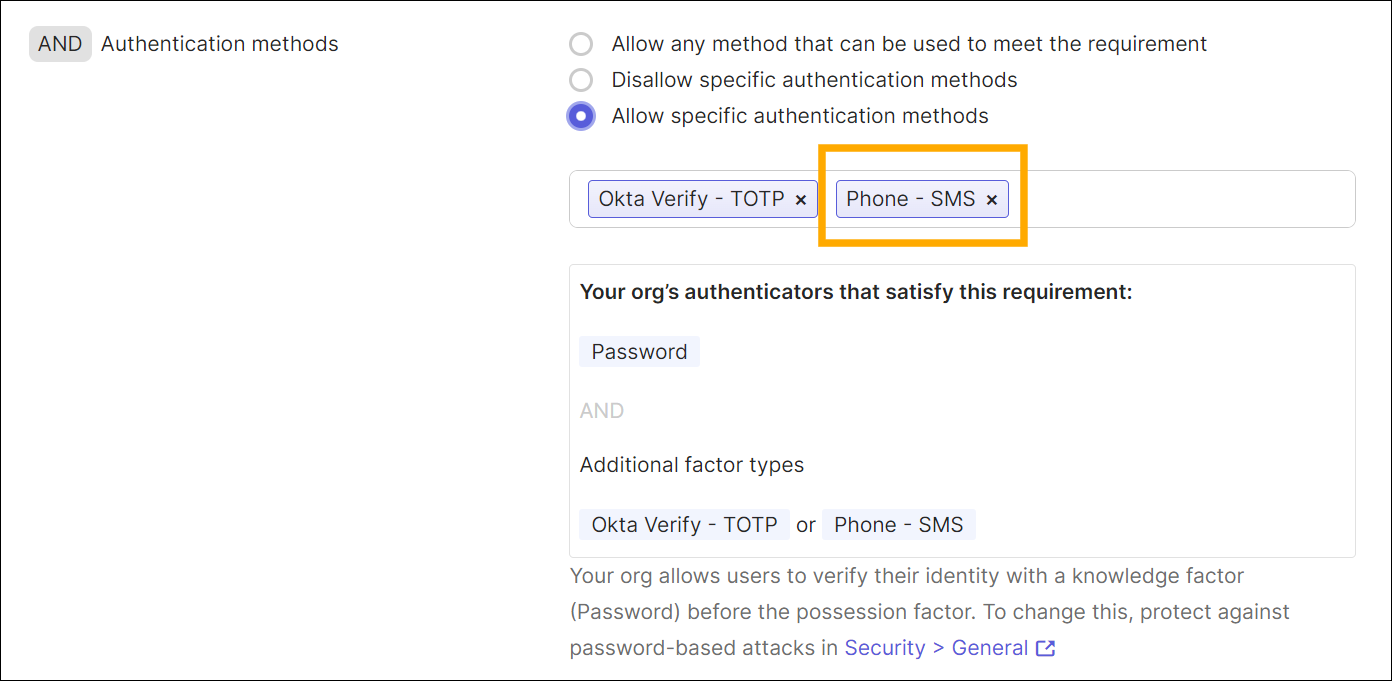
Make sure that the Authentication methods section includes Phone Authenticator.
In SMS delivery, Sinch will respect the message template provided by Okta, excluding selected countries for legal reasons:
- Kuwait
- United States
- Singapore
- United Arab Emirates
- Libya
In those countries sending business messages requires preregistering them within the government. Sinch will use one of the approved SMS templates, instead of arbitrary ones provided by Okta. To customize SMS messages for those destinations, contact Sinch support.
To customize voice messages, contact Sinch support.
If processing fails on the Sinch side or if your account lacks sufficient credits, Okta will attempt to send the OTP using its telephony providers.